“Life under quarantine” brought on by the COVID-19 novel coronavirus pandemic has accelerated the digital transformation. The video conference app Zoom has largely replaced face-to-face meetings. Now there is one more thing that the world has to deal with: zoombombing! This may only be a foreshock. In the previous article, we raised the question, “Are you really meeting with the person you think you are meeting with on Zoom?” So, what happens if they are not the person you think you are talking to? What if the real tremors are still impending on Zoom?
A security issue was bound to ensue once the number of Zoom users increased twenty-fold in three months. Zoombombing attacks, or Zoom raids, by uninvited guests can easily infiltrate video conferences or training sessions on Zoom. Hacking these sessions with inappropriate images and words has instantly caused a furor. It has been at the top of the agenda as if it was the only thing to worry about. In the United States, video conference hacking is now considered a “federal crime,” following a security statement made by the New York attorney general’s office, FBI’s Boston bureau, and Eric Yuan, Zoom’s CEO, in early April. In response to these rising Zoombombing attacks, the United States Attorney for Eastern Michigan issued a written statement on April 3, which asserted, “Disrupting a public meeting, invasion of a computer, using a computer to commit a crime, committing a hate crime, committing fraud or making a threat in this way may be punishable by fines and imprisonment.
US attorney may be trying to elude to deepfake
Matthew Schneider, United States Attorney for Eastern Michigan, said in a written statement that “If you interfere with a teleconference or public meeting in Michigan, you could have federal, state, or local law enforcement knocking at your door. You think Zoom bombing is funny? Let’s see how funny it is after you get arrested.” While discouraging Zoom hackers with the long arm of the law, he also expanded the definition of possible risks. Zoom hackers could hack not only into Zoom sessions but also into the participants’ cameras, compromising their private photos and secret and personal information. However, he did not even consider what Zoom hackers can do under the deepfake mask.

What if it wasn’t the real Boris Johnson on the Zoom screen?
Before he was diagnosed with the coronavirus and put in intensive care in the UK, Prime Minister Boris Johnson had a COVID-19 meeting on Zoom during the first days of self-quarantine at his home. Among the many possible attendees were ministers, high-ranking bureaucrats, and scientists. The health of the community and the future of one of Europe’s strongest nations were being discussed at the highest level, and it is possible that they were making decisions not only about the United Kingdom but also about the world. The UK spearheaded the “herd immunity” exercise in the world, giving the novel coronavirus free rein. In the end, when the prime minister’s COVID-19 test turned out positive, they had to make a U-turn and impose the quarantine measures. So, during those days, instead of the prime minister of the UK, what if it were a hacker with a Boris Johnson deepfake mask, imitating his voice on the Zoom screen? What if the hacker told the ministers and bureaucrats that the quarantine measures were not necessary? When Boris Johnson himself was performing so poorly with COVID-19, what would his impersonator mimicking his face and sound cost the empire where supposedly “the Sun never sets”?
Masquerade ball precedes the invention of deepfake
On March 11, a Paris court sentenced Gilbert Chikli, one of the Franco-Israeli defendants, to eleven years in jail and a $2-million fine. Meanwhile, Anthony Lazarevitsch, his partner in crime, received seven years of prison time and a $1-million fine. From 2015 to 2016, these two men dumbfounded everyone by simply using silicone masks to do what deepfake can do today. During the two years of this masquerade, 54-year old Gilbert Chikli and 35-year old Anthony Lazarevitch managed to trick people by constructing a silicone mask of Jean-Yves Le Drian, the former defense minister and current foreign minister of France. The duo swindled $55 million from prominent people in their criminal enterprise. The Guardian reported that these fraudsters targeted more than 150 wealthy businesspeople, politicians, and religious figures whom they duped with a video conference invitation made over the phone or Skype.

Ringleader Chikli put on a silicone mask to impersonate the French minister Le Drian wit h a duplicate of the minister’s office appearing as a backdrop. Crooks scammed their wealthy victims under the ruse that they needed financial aid to save the captives of religious terrorist organizations in the Middle East, especially in Syria. They made the biggest heist in 2016 when Karim Aga Han made five separate deposits of $20 million into the Polish and Chinese account numbers they had provided. Though three of the transfers stopped at the last moment, $7.7 million was never recovered. A couple of months later, it was reported that Turkish businessman İnan Kıraç was also tricked into sending $47 to the grifters as ransom money for two journalists kept hostage in Syria. Their third victim was Corinne Mentzelopoulos, a French-Greek businesswoman, known for her world-famous Port wine and property investments. She lost $5 million. Some of their other unsuccessful attempts included Gabon’s president Ali Bongo, the French AIDS charity Sidaction, chief executive of the cement co mpany Lafarge, and the archbishop of Paris. Chikli tried the same scam for the second time 10 years apart. He received a seven-year prison sentence in 2015 for similar racketeering attempts between 2005 and 2006. Chikli’s scam stories inspired the 2015 French movie Je Compte Sur Vous (I’m Counting on You).
Does deepfake pose a threat to COVID-19 fund drives?
Chikli was caught, along with his accomplice Lazarevitsch, in Ukraine. When they were arrested, they had silicone mask photos of Prince Albert of Monaco, whom they had not yet had time to mimic. There is something far more convincing than a silicon mask: a deepfake synthetic media that is created with machine-learning algorithms using artificial intelligence (AI) technology and artificial neural networks. So, with the dawn of deepfake, it may be that the era of silicon masks is now over. Hackers no longer require silicon masks of a minister, prime minister, or president to scam people. This comes at a time when the television reports that leaders, such as Boris Johnson, are holding all of their meetings on Zoom or other video conference apps, and that countries and international organizations around the world are launching massive fund drives for the COVID-19 pandemic. How many people would actually dare to double-check the authenticity of a political leader who appears on their comp uter or telephone screens? You decide.

Is it that easy? Take a look!
Up until now, you may have thought of deepfake as fake videos that are created to be indistinguishable from the original by using special algorithms with the help of artificial neural networks and deep learning. In that case, you may also believe they only consist of videos prepared in advance. However, AI technology makes live deepfakes possible. So, don’t be so sure that the image on the screen is the person you think you know when you answer a video call on apps such as Zoom, Whatsapp, Skype, or Facetime, all of which have that feature. It very well may be that there is someone malicious behind the image or sound, pretending to be someone you know to set a dreadful trap for you.
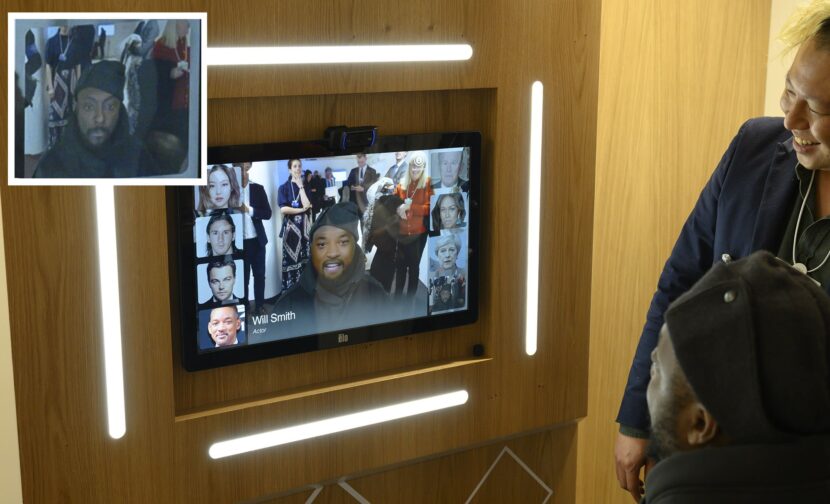
Hao Li, the associate professor of computer science at the University of Southern California, is internationally known for his research on deepfake. The MIT Technology Review described him as the “world’s best deepfake artist.” Recently, he put on an impressive show with a team from Pinscreen, the company he founded and now leads as its CEO. Hao Li and the Pinscreen team demonstrated real-time, interactive face-swapping during the World Economic Forum (WEF) in Davos, Switzerland, in January 2020. They made the attendees appear as celebrities such as Michelle Obama, Lionel Messi, Leonardo DiCaprio, and Will Smith on a live and real-time “Deep Mirror” on special screens. Pinscreen’s research aimed to advance “new deep learning” and “data-driven geometry processing algorithms.” The technology allows users to swap faces with those of famous people on a virtual mirror, heralding a step further for deepfake. Classic deepfake technologies require data. In contrast, the new beta zone technol ogy by Hao Li and his Pinscreen team works instantly, swapping a person’s face with that of another without needing to be trained. Face-swapping happens in real time.
Virtual deepfake cameras coming soon
Do you think this technology is still some time away from appearing on Zoom? Take a look at seemingly innocent and entertaining Aphrodite.ai. This application lets you create a deepfake in real time by using your computer’s web camera. At the moment, the beta version works only on desktop systems that use the latest versions of Chrome and Firefox. And, the development process is in the works. The Aphrodite.ai team is said to be working on a standalone application that allows the transformed video to be used as a virtual camera on Skype or other video conference applications.
Don’t Zoom without zooming in on the participants first
Make sure to err on the side of caution with online security while using Zoom and other video conference apps. It will not be too long before we find out if an effective deepfake detection model will emerge as a result of Facebook’s Deepfake Detection Challenge (DFDC). In any case, we must keep hope alive and continue to protect ourselves, just as we do against the coronavirus pandemic. Don’t use applications, such as Zoom, that do not offer end-to-end encryption just because you want to jump on the bandwagon. In order to increase security during your Zoom meetings, use a temporary user ID each time and activate the Waiting Room feature to see who is attempting to join the meeting. Also, go to Settings to disable the “Join Before Host” and other risky features. Finally, once the invited attendees join and the meeting begins, lock the meeting to outsiders.
It is like a madhouse out there because of COVID-19, and what may be lurking around the corner is anyone’s guess. You may receive an unexpected video call from someone you cannot say no to. It is better to be safe than sorry. Keep vigilant!